It’s not the newest trend. In fact, it’s rather old news. It’s still important to use strong passwords, use passphrases, and YES! Passwords really do still get cracked. The many techniques for obtaining passwords over the years have become more sophisticated, but the tried and true methods still work. The top methods for cracking passwords, in no particular order are rainbow tables, brute force attacks, social engineering, phishing, malware, and plain old guessing.
The more complex your passwords are, the less likely they will end up in the hands of a cybercriminal. The age-old advice for selecting passwords still remains true:
- Combine upper and lower case letters.
- Use no less than eight characters. Passphrases are best.
- Include at least one number and one special character. More of each is better.
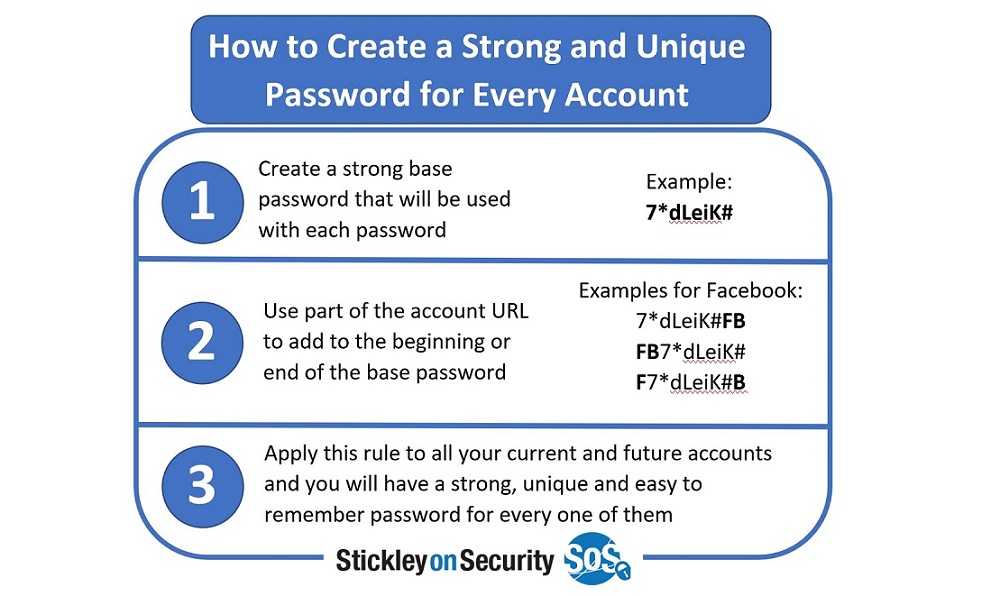
- Make them easy to remember, but difficult to guess. For example, make them create a pattern on the keyboard or use a base phrase and add to it based on the website name.
- Having strong passwords is important. Sometimes knowing why is helpful. One reason is because time is money; even in cybercrime. The easier the password, the easier and faster it is to crack. It’s as simple as that.
Criminals often crack passwords en masse, so when they get enough easy ones figured out, they move on to the next phase of their crime and dump the ones they can’t figure out quickly.
Knowing how they end up in the hands of the cybercrime world may help in understanding why it’s so important. So let’s get back to those aforementioned methods.
At a high level, rainbow tables are long lists of every possible plain text permutation of encrypted passwords. Attackers use these in password cracking software and can try a lot of passwords in a short period of time, depending on the size of the list. Thus, security experts recommend using longer passwords and phrases. The longer they are, the more time it takes for them to be found in these lists.
Brute force attacks use dictionary words working through all possible combinations of alpha-numeric characters from AA1 to zz1. These are not quickly done, but often those who use them have a lot of time on their hands and it’s worth the effort. In any case, the longer the password, the longer it takes to figure it out.
Social engineering is the foundation of so many security related breaches; whether they are intrusions into a network, theft of a password to get into an account, or getting malware onto a computer. At a basic level it involves getting users to give up passwords or access. Hackers are amazingly successful at getting information by pretending to be someone else and bringing victims into their confidence. A favorite scene for the social engineering actor is to call workers in an office posing as the IT person. They simply ask for passwords and surprisingly and unfortunately, it really works.
Phishing should be familiar to everyone by now. According to IBMs X-force researchers, phishing increased four times in 2017 over the previous year. And it’s not only increasing in volume, it is evolving and getting more sophisticated. It’s getting to a point that identifying phishing is nearly impossible, even for the most educated on the topic. Currently, it’s estimated that more than half of the email we receive is spam. Most of it gets caught in spam filters, but much of it doesn’t. Of the messages that make it to users’ in boxes, about half are opened. Roughly 10% of those are acted upon. These messages are trying to coax the users out of information and often times it’s a password to some account that will net the thief something of value.
Next, there is malware. This is software that ends up on a computer or device and can be used for any number of activities from logging key strokes (key loggers) to redirecting a web browser to fake websites to collecting administrator rights to networks.
Finally, there is the highly unsophisticated method of guessing. Believe it or not, it still works. People often create passwords based off of information that is not so hard to find out such as kids’ names, birthdates, pets names, etc. This is especially true with the rise in popularity of social media and networking websites. People post their kids’ names, birthdates, pets’ names, their travel plans, addresses and so forth on their social media profiles. A savvy hacker may use the previously discussed social engineering techniques to befriend victims and simply guess passwords.
There are many more strategies for getting passwords. No matter what you come up with for yours, it needs to and should make sense to you and no one else. If you must write them down, do it. Just keep it separate from your computer and mobile device and keep it out of plain sight. And if you can use clues to trigger your memory, that’s better than writing out the passwords in their entireties.
We have a lot of passwords these days used for everything from online magazine subscriptions to logging in to check our healthcare information. We trust many others with our sensitive information and the only thing between us and that information is still quite often, only a password.
Protecting that information is critical. Following are some guidelines regarding passwords and protecting them as well as the information they protect:
- Don’t use words commonly found in any dictionary for your passwords; even in foreign language dictionaries. Don’t use slang terms or phrases either. The bad guys are onto that too. If you are thinking of substituting an “1” with the lower case “L,” don’t bother. That’s an old trick. Spelling words backwards or with common misspellings; they know those too and even use those for other trickery.
- Never include personal details in passwords such as your name, birthdates of your kids or loved ones, or even pets’ names. Those are not all that difficult to find out anymore, so don’t make it easy on someone with ill intentions.
- When your password recovery options ask which questions you want to choose, pick ones that are not obvious and few people know the answers to; better yet, make up your answers. Just don’t forget what you chose, if you decide on this strategy.
- Several studies have found out that using device default passwords is still common. Year after year, “12345” and derivations of it still top the most commonly used password lists. The number 2 password is “password.” Be more creative than this.
- Password reuse is common and is still a bad idea. This means using the same password for multiple accounts. Yes, using so many different ones may seem daunting, but it’s important. It’s particularly critical to make sure your social media, healthcare, and financial account passwords are completely different from one another and from everything else.
- When using public computers, in a hotel business center or internet café when traveling for example, make sure that the box to remember your password is NOT checked and be sure to close out the browsers you used before leaving. Otherwise, someone may use the computer after you and get access to your accounts or be able to view what you just did.
- If you are sitting in a coffee shop enjoying a cup of joe and decide to check out the Internet using their free wireless, avoid logging into any of your accounts that have sensitive data, including your work accounts. Hackers are often found lurking in these places using programs to intercept passwords. If you need to check something and it can’t wait till you get to a secured location, use the data network on your smartphone rather than the wireless. If you’re logging into your office from a remote public location, use a VPN.
- It may seem obvious, but it happens a lot. Don’t tell anyone else your passwords. This includes anyone from your IT department. They just don’t need them. If you just cannot remember it, reset it.
- Make it a routine to change passwords to online accounts regularly. It is recommended to do this at least once every three months.
It’s OK to have online accounts. They are convenient and help us stay on top of information and help us do our jobs. Just keep basic security guidance in mind when using them.
© Copyright 2018 Stickley on Security Inc.
 An official website of the State of North Dakota
An official website of the State of North Dakota
